I am able to produce a binary with Clang that has either a stack canary or SafeStack protection, but not both. SafeStack seems to take precedence if both the '-fstack-protector-all' and '-fsanitize=safe-stack' options are specified. Are these Clang options mutually exclusive? I cannot seem to find anything elsewhere pertaining to this issue. My goal is to produce a binary with both protections which should be possible as far as I'm aware. Any guidance would be sincerely appreciated.
My Clang and FreeBSD versions are below along with relevant output. The 'checksec' script below calls 'readelf' to check for certain symbols in the ELF binary. The script source can be viewed/obtained here if desired: https://raw.githubusercontent.com/slimm609/checksec.sh/master/checksec. In this context, the script is looking for the following symbols:
Stack Canary
SafeStack
I have a few questions about Stack Guard and SSP protections. First question is about Stack Guard and its three types of canaries, if I am correctly - terminator, random and random XOR.
Use Stack Protector All (stack Canaries For Macbook Pro
1) I'd like to know, how to disabled Stack Guard on x86 Linux system? Somewhere I read, it's possible with this command, while compiling with gcc '-disable-stackguard-randomization', it's same like with this command for enable '-enable-stackguard-randomization', both doesn't work. If needed, my gcc version is 4.8.2.

If I'm not mistaken, if you want to enable stack smashing protection in an iOS app built with XCode, you need to specify the –fstack-protector-all compiler flag. Is there some analogous action in X. Then if./pdnshw; then echo Everything ok, now run $(MAKE) using same settings (if any) you passed./configure; else echo Could compile binary, but not run it, read README please; fi; 4 pdns/build-recursor. PROBLEM DESCRIPTION: The ehframe saved on the stack was corrupted by the store of the stack guard canary value. When unwinding happens, a crash occurs. USERS AFFECTED: Users of -fstack-protector-strong and pthreads. Problem conclusion. The store of the canary word was corrected and the generated frame is now safe for unwinding.
2) Next question about Stack guard, when I will able to enable/disable it, how can I set, which type of canaries I want to use? What I read, terminator canaries are used by default, for random I have to compiled with '-enable-stackguard-randomization', but how about random XOR? (Or with null 0x00000000)
Use Stack Protector All (stack Canaries For Macs
3) Now about SSP(ProPolice), I know, for random canary I have to compiled with 'fstack-protector-all', but how about terminator, is it same as in Stack Guard, by default?
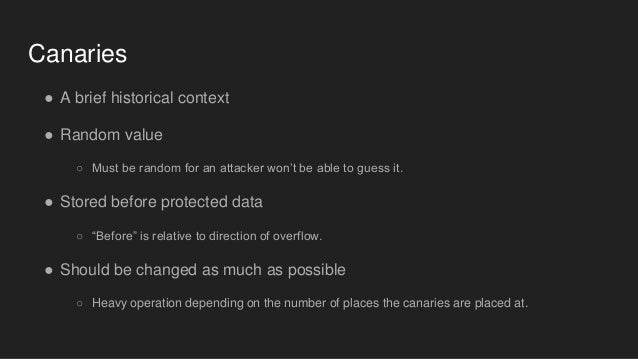
4) Last one, if anyone of you, can tell me, where I can find random canary in memory. For example, I have this scenario - compiled C program, like 'gcc -g example.c -o example -fstack-protector-all', so with random canaries. Let's say, I'm able to get address of canary, after every execution. So expect, I have: Canary = 0x1ae3f900. From a different papers, I get some info, that canary is located in .bss segment. Youtube crtaci. So I get address of .bss segment using readelf: 'readelf -a ./example | grep bss'. It's 080456c9. In gdb I set some breakpoints, to get address of canary, but when I check .bss address x/20x 0x080456c9, all I see are only 0x00000000 addresses, butcanary is nowhere. Plus, I checked __stack_chk_fail's if it isn't there, but with same result, I can't see it there. I get address of stack_chk_fail from PLT/GOT.
Thank in advance for your answer and time.
Use Stack Protector All (stack Canaries For Mac Os
I have a few questions about Stack Guard and SSP protections. First question is about Stack Guard and its three types of canaries, if I am correctly - terminator, random and random XOR.
Use Stack Protector All (stack Canaries For Macbook Pro
1) I'd like to know, how to disabled Stack Guard on x86 Linux system? Somewhere I read, it's possible with this command, while compiling with gcc '-disable-stackguard-randomization', it's same like with this command for enable '-enable-stackguard-randomization', both doesn't work. If needed, my gcc version is 4.8.2.
If I'm not mistaken, if you want to enable stack smashing protection in an iOS app built with XCode, you need to specify the –fstack-protector-all compiler flag. Is there some analogous action in X. Then if./pdnshw; then echo Everything ok, now run $(MAKE) using same settings (if any) you passed./configure; else echo Could compile binary, but not run it, read README please; fi; 4 pdns/build-recursor. PROBLEM DESCRIPTION: The ehframe saved on the stack was corrupted by the store of the stack guard canary value. When unwinding happens, a crash occurs. USERS AFFECTED: Users of -fstack-protector-strong and pthreads. Problem conclusion. The store of the canary word was corrected and the generated frame is now safe for unwinding.
2) Next question about Stack guard, when I will able to enable/disable it, how can I set, which type of canaries I want to use? What I read, terminator canaries are used by default, for random I have to compiled with '-enable-stackguard-randomization', but how about random XOR? (Or with null 0x00000000)
Use Stack Protector All (stack Canaries For Macs
3) Now about SSP(ProPolice), I know, for random canary I have to compiled with 'fstack-protector-all', but how about terminator, is it same as in Stack Guard, by default?
4) Last one, if anyone of you, can tell me, where I can find random canary in memory. For example, I have this scenario - compiled C program, like 'gcc -g example.c -o example -fstack-protector-all', so with random canaries. Let's say, I'm able to get address of canary, after every execution. So expect, I have: Canary = 0x1ae3f900. From a different papers, I get some info, that canary is located in .bss segment. Youtube crtaci. So I get address of .bss segment using readelf: 'readelf -a ./example | grep bss'. It's 080456c9. In gdb I set some breakpoints, to get address of canary, but when I check .bss address x/20x 0x080456c9, all I see are only 0x00000000 addresses, butcanary is nowhere. Plus, I checked __stack_chk_fail's if it isn't there, but with same result, I can't see it there. I get address of stack_chk_fail from PLT/GOT.
Thank in advance for your answer and time.